H1-2010 Bonuses
Note: Verizon Media is now known as Yahoo.

During this event, we will have a few bonuses up for grabs in each round of the event. Read on to learn how you can earn them!
Hacker of the Day
Each day, around 5pm ET, a tweet from @theparanoids will announce the Hacker of the Day!
The Hacker of the Day will be chosen daily based on report impact, report write up quality, and positive contributions to the community. The winner will be notified beforehand allowing an opportunity to provide their Twitter handle for inclusion in the tweet (optional).

Best Report
What does Verizon Media look for in a good report?
An extra few minutes on a report can potentially save you hours once it has been submitted. Remember, the issue may be clear to you, but if it cannot be replicated with easy to follow instructions you will likely receive this status change:

At this point, you may have to rewrite your whole report again - when this time could have been spent looking for another vulnerability aka $$$$. Take a moment to review with us the key components of a good report.
Assets

Verizon Media has a large presence on the internet. Select the asset that aligns as closely as possible with where you found your vulnerability.
Weakness

Severity
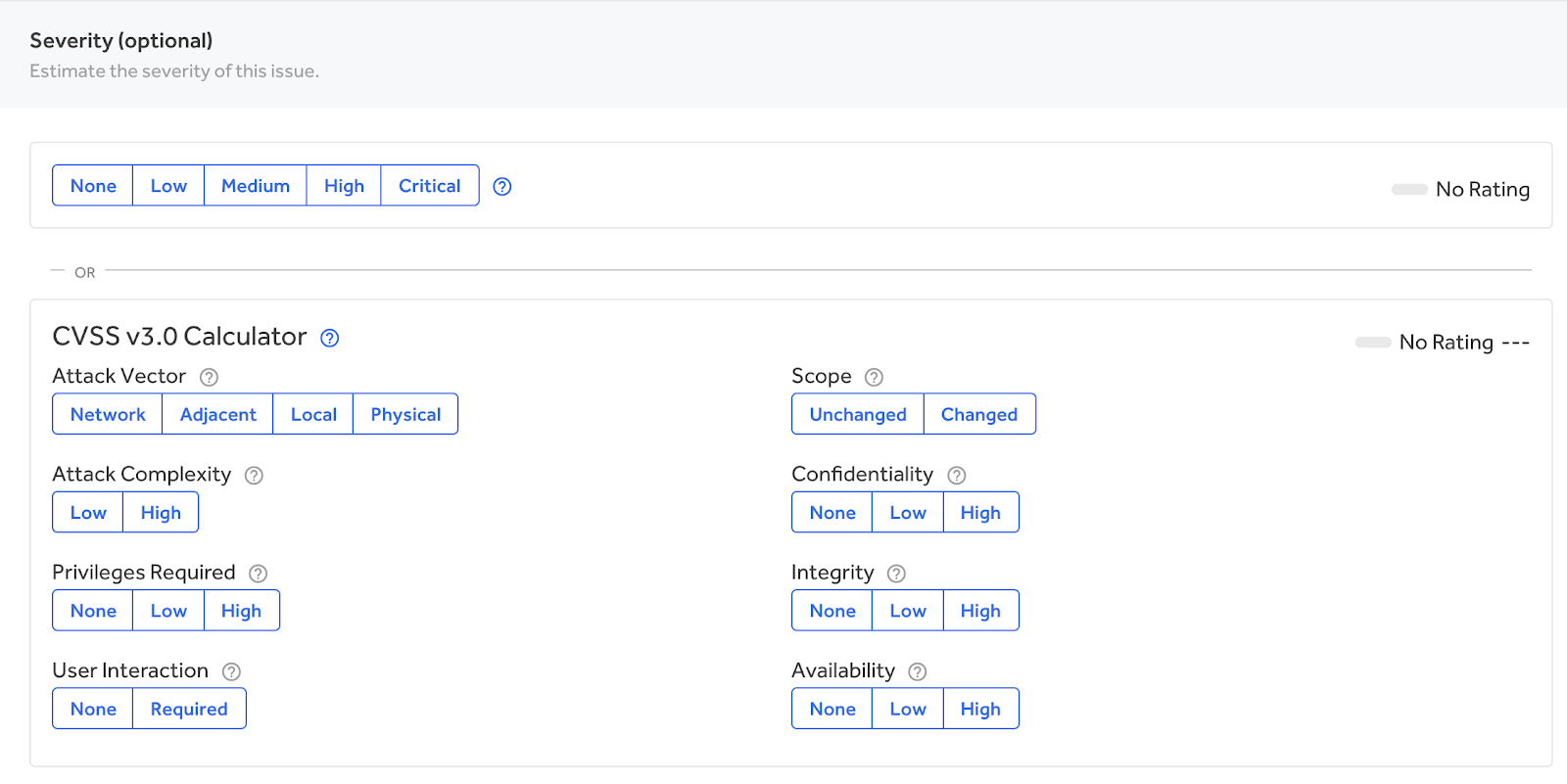
While optional, this part of the report is usually the most contentious as it directly correlates to a potential bounty award. Try and be as honest as possible with yourself and us. Marking a report as critical all the time does not work in your favor and it does not help you jump the queue. We read every report with fresh eyes, but if you have trained us to expect that your severity is wrong, it may be hard to change that perception.
It should be noted that Verizon Media will make the final determination on impact. At times we have reduced severity and provided an explanation as to why and other times we have increased the impact after further internal investigation.
Proof of Concept

Title
It’s a simple field, but can be an effective tool in drawing attention to your report. The title is displayed within H1 email submission reports and within the H1 inbox. This is a good chance to roll together the asset, attack, and result into one line.
Example: "UnAuthenticated Boolean Based SQLi - foo.bar.media.yahoo.com"
Summary
Start with a one paragraph description of your report. This is the first text we read - is it enough to convince us you found an issue? Some additional items to include within the summary are:
Steps To Reproduce
If this section is not clear in your report, expect the status icon (purple) on the report to turn to light blue (bad) instead of going orange (good).
Below are some simple considerations:

Some of the best reports we have seen also include a detailed explanation of how the hacker came to testing this specific thing, and why they tried this type of attack in that place.
- If you are able to script an exploit for the issue, this is a great value-add. For example - POC.py
- When hosting remote files (HTML / SVG / PHP) etc, paste the code into your report so Triage can create their own POC’s on their own servers.
- Consider including a POC video; these are useful for a number of reasons. (1) it shows the vulnerability working at that given time (2) in multi-step reports, it can clearly show the whole process through to the final exploitation
- Always include poc scripts, screenshots, videos within the H1 report. Never upload anywhere else.
Hopefully this overview is useful to level up your report writing skills. We certainly hope so!
Happy hacking,
The Paranoids